How to detect ddos attack on windows to keep you safe

What is a DDoS Attack?
Have you ever been stuck in traffic on the way to something important, but the road is flooded with cars? DDoS (Distributed Denial of Service) attacks work in a similar way, but in the digital world. Hackers overwhelm a system by flooding it with a massive amount of unnecessary requests or inputs, much like a road filled with too many vehicles, causing traffic to come to a standstill. This flood of traffic overwhelms the system, preventing normal operations and causing it to crash.
DDoS attacks are typically carried out using a network of compromised computers, known as a “botnet.” These attacks aim to disrupt regular traffic so severely that the system can no longer function effectively. DDoS attacks come in various forms, each targeting systems in different ways. It’s important to note that DDoS attacks are not limited to personal computers like Windows PC or MacBook—major corporations often face the challenge of defending against these attacks as well.
Most Common types of DDOS attacks
DDOS attack on your system in different ways.To mitigate the attack you first need to understand what kind of attack it is. DDOOS can be of various types like.
1. SYNC Request Flooding: In this attack, your network is flooded with a large number of SYN (synchronization) requests, disrupting the normal handshake process.
2. HTTP Flood attack: This attack targets web servers running on Windows by overwhelming them with a large number of HTTP requests. The flood of requests saturates the server, consuming resources and making it difficult for the system to handle legitimate traffic.
3. UDP Flooding: In this attack, the system is flooded with a large number of User Datagram Protocol (UDP) packets, designed to keep the normal system busy. This influx of traffic can overwhelm the network resources, causing disruptions in service.
4. Application layer attack: These attacks focus on the server layer responsible for generating web pages. They aim to flood resources, blocking legitimate access and disrupting normal website functionality.
5. DNS Amplification attack: A DNS amplification attack involves sending lookup requests to an open DNS server with the target’s spoofed address. This tricks the server into sending volume of responses, flooding the victim with excessive data.
6. PING Attack: This attack disrupts a system by sending packets that exceed the size limit. When the attacker delievers these oversized packets, it can cause a ping attack, leading to buffer overflow issues.
How they can be really dangerous for your windows
In 2024, with many businesses operating online, your work PC can be a valuable target for hackers for their financial benefits. A DDoS attack could lead to serious financial losses, with a Kaspersky study revealing that such attacks can cost companies over $1.6 million.
Even if you’re not running a business, you should still be concerned. DDoS attacks can impact you by making critical services, applications, or websites on your Windows system unavailable due to overwhelming traffic. Your personal computer may also become sluggish or unusable.
So, how can you tell if your Windows system is under a DDoS attack?
How can you detect DDOS attack on Windows
The initial step in addressing a DDoS attack is recognizing it. Windows offers various built-in tools and features designed to help identify abnormal traffic patterns.
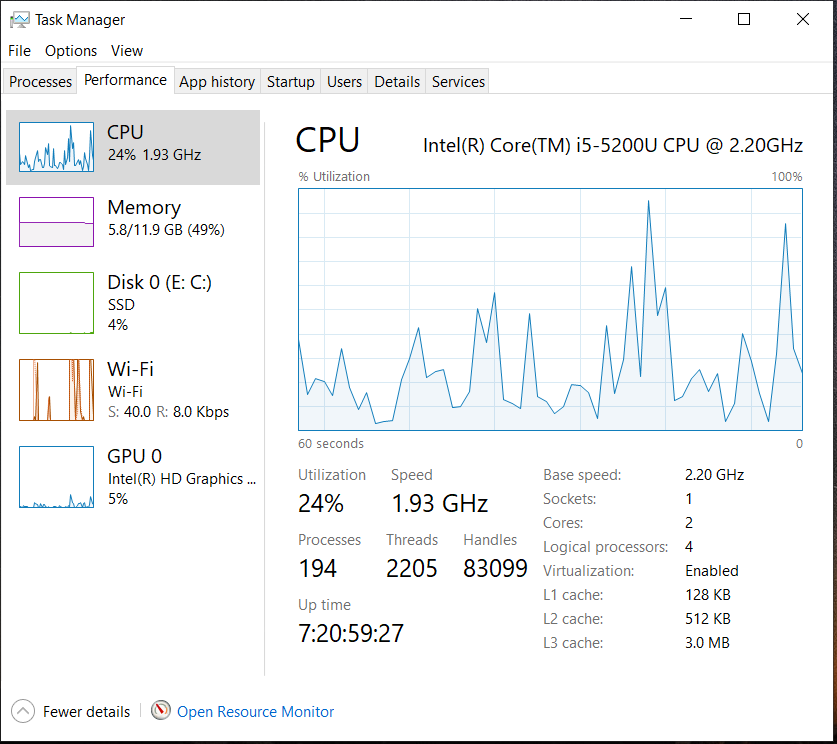
Monitor your traffic with Task Manager
If you feel any sudden spike or abnormal activity you can go for detailed scan.
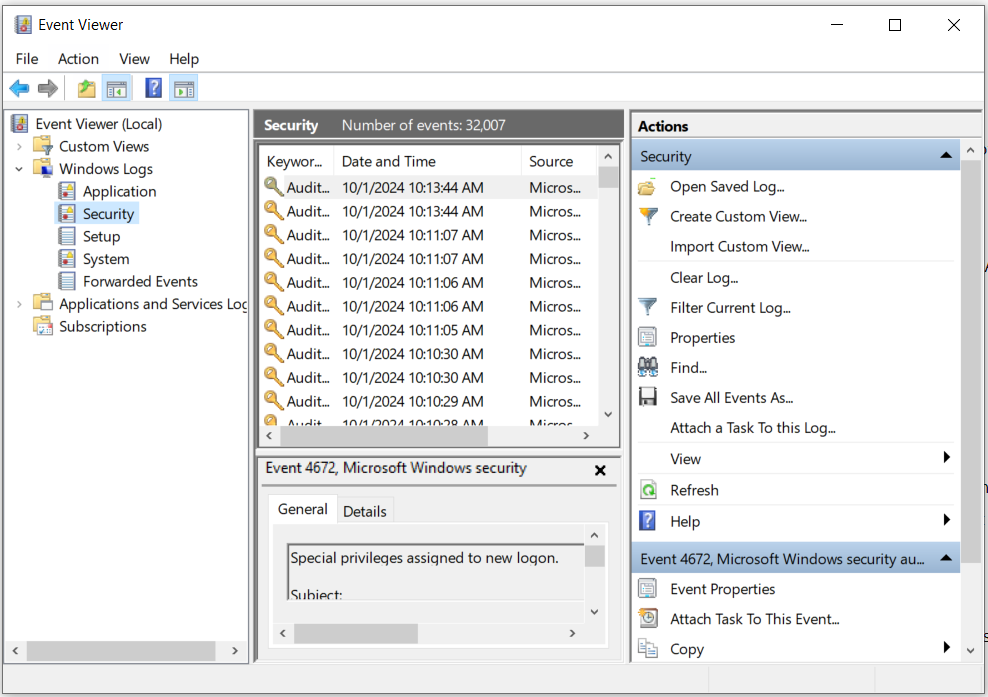
Regular logs moniitoring with Windows Event Viewer
Look for warnings, errors, or sudden packet drops related to networking, as these can be signs of a DDoS attack. Additionally, monitor for any unusual or frequent system reboots, which could indicate your system is being affected by malicious activity.
Check Performance Monitor
Analyzing Bandwidth with Netstat
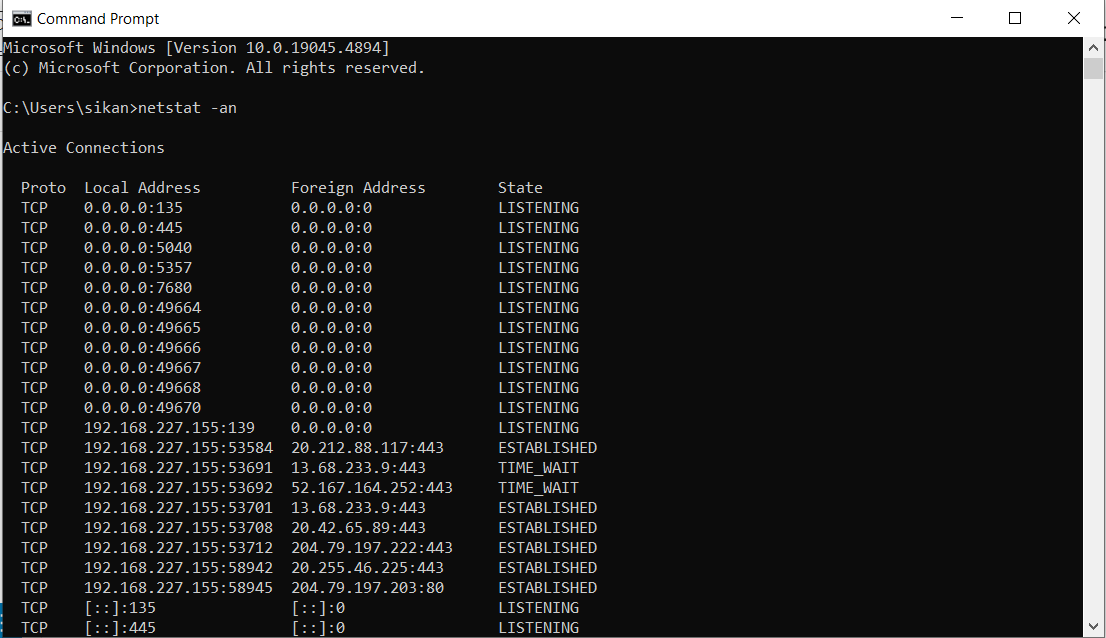
See traffic STats using Third parties tools
Third-party software can offer advanced detection capabilities and more detailed analytics. Wireshark is a popular network protocol analyzer that captures network packets in real time. GlassWire is a user-friendly tool that offers detailed network monitoring
Manual Pinging
How to respond to DDOS
If you believe your system is under a DDoS attack, the first step is to immediately disconnect it from the network to minimize further damage, as these attacks typically occur when you’re online. After disconnecting, configure your firewall to limit incoming traffic and prevent the system from becoming overflooded by restricting the size and number of connections allowed.
Additionally, ensure that your system is up to date with the latest security patches, as updates often include fixes for vulnerabilities that attackers might exploit. However, before applying any updates, make sure to back up your important data to avoid potential data loss. Staying proactive with backups and updates is crucial to maintaining a secure and stable system during and after an attack.
