is tor browser safe

What is TOR Browser
Tor Browser anonymizes users’ web traffic through the Tor network, thereby securing their identities while browsing the internet. You may have heard of onion routing at different times. As the name implies, it may link to the onion layers. Onion routing is the process of wrapping data in multiple layers of encryption, similar to the layers of an onion. The Onion Router encrypts traffic using a network of volunteer-operated servers known as nodes.
To keep things simple and avoid technical jargon, when a user searches for something on the Tor browser, their traffic is routed via at least three different relays before arriving at its final destination. Relays in the Tor network are like checkpoints on a secret trail that your internet traffic passes through to remain anonymous. To learn more about the relays used by the Tor browser, see types of relays on the Tor network.
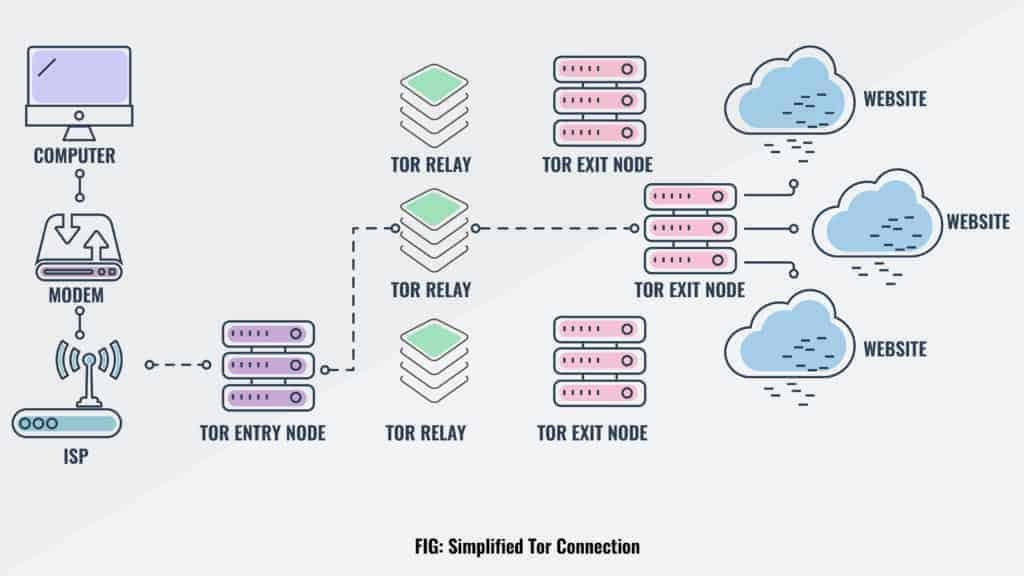
What is TOR Relay
To give you an idea of relays, the TOR browser routes your traffic through three main relays (stops).Entry, middle, and exit relays. The entrance relay is the first point that knows your IP address but not your destination. The middle relay serves as a secure bridge, and the exit relay knows the destination but not your IP address. Tor ensures that no single relay knows your identity and destination by routing traffic through them and utilizing layered encryption.
The browser provides access to websites prohibited by ISPs or the government. Tor browsing may be slower than the open internet. The rationale for this is that it gives increased privacy and anonymity, but these benefits come with a cost of speed due to many relays, encryption and decryption, and additional security procedures. Some governments prohibit anonymous communication, making Tor illegal. However, its legality is dependent on the country in which you use it. You can explore countries that have banned Tor.
Around 2011, China launched a concentrated effort to block known TOR nodes. The Great Firewall of China (GFW) began to considerably increase attempts to prevent TOR.
The are million of user of TOR worldwide but Is TOR Browser safe to use in 2024?
Level of Security
Tor Browser offers several layers of security to protect user’s privacy and data integrity. These levels include built-in features and best practices such as Onion Routing. Tor encrypts data as it passes through a series of nodes. Each node decrypts enough information to get the idea of trustworthy receiver, where privacy would be preserved. The Route Obfuscation is a path through which the network changes periodically making it difficult to track the activity.
How enhance TOR Security
Security is enhanced through HTTPS connections wherever possible ensuring that data transmitted between the user and the site is encrypted. Moreover, the NoScript extension blocks potentially malicious scripts from running on websites reducing the script-based attacks. The general security levels are Standard and provide onion routing and encryption, Safer which disables additional web features for increased security, and the Safest which disables JavaScript on all web-sítes.
Must read: IS Opera GX Is A Safe Browser? Comparion With Chrome,Firefox And Others
Is Tor Safe
Tor is usually regarded as safe and secure due to its onion routing system. However, it is vulnerable to a variety of risks including phishing scams. The TOR Browser can only protect your anonymity if you use proper operational security procedures. But keep in mind that everything connected to the internet is not completely safe. JavaScript and browser plug-ins can be used to reveal your identity. TOR Browser disables these by default, however users should exercise caution before enabling them.
How to keep yourself safe on TOR
If a user signs into a website using an email account via Tor, those services may nevertheless record the user’s activities. To keep safe on Tor, take additional precautions such as installing a VPN, firewall, and antivirus software. If a highly professional individual establishes a connection between the entry and exit nodes, he can obtain your identity. However, it is not easy. In comparison to standard Chrome, Firefox, and Opera browsers, TOR is regarded as secure and reliable.
• To change Tor security to safest mode click the shield icon in the top right corner.
• Go to settings and scroll to the security level where you can choose the safest.
Is Tor Illegal
Tor is perfectly legal to use as long as you do not engage in illegal activity. The Browser is not illegal in every country, but its legality varies according to local laws and regulations. China is the primary source of browser resistance. The Great Firewall of China blocks known TOR nodes, and using TOR can result in penalties. Russia and Saudi Arabia are working hard to prevent the general public from using Tor. Iran and Turkey have restricted access to Tor.
Tor is legal, and the network is funded by the United States government. It is extensively used by journalists, activists, and privacy-conscious people. Repressive regimes dislike Tor because it allows journalists to easily report on corruption and assist dissidents facing political repression. Tor supports freedom of expression in a democratic territory.
Users can perform activities to stay legal and safe on Tor.
• Know the Law
• Use Tor Responsibly
• Stay informed
• Avoid Illegal activities
Click to read Top safe Browsers in 2024
Core features OF TOR
Tor browser promises privacy and anonymity by routing internet traffic. The distributed network of relays creates a secure path that masks location from websites and surveillance attempts. Onion routing encrypts traffic multiple times before sending it through a series of relays across the globe. Each relay decrypts one layer of protection and encryption making tracking impossible. The exit node sends traffic out to the internet publicly. Tor browser also blocks scripts by default.
Moreover, through Sandboxing Tor isolates each website users visit. This prevents malicious code from one site affecting other sites on device. Users can also start with a new identity every time users open it. These steps provide extra privacy and security on Tor browser.
How SeCure and Risky is TOR
Tor browser shields privacy and anonymity but it also purveys some potential risks and vulnerabilities. Exit node is one of its major risks. These nodes deliver data to the final destination. If a malicious agent controls an exit node, your data is exposed or malware can be injected. Similarly, accessing malicious sites through Tor can still infect the device.
Tracing users, however, is difficult with Tor but not impossible. Law enforcement agencies have advanced resources that may track users’ activities through traffic analysis. Tor is often associated with Illegal activities and the web. This increases suspicion and scrutiny from ISPs and authorities. Tor anonymizes users activity not identity. High value target may get attacked by determined attackers.
Practical Tips to enhance safety
A little extra caution is required on every path you choose. Choosing a reputable exit node from a trusted source encrypts data as exit nodes are a potential risk. Users may consider switching nodes periodically. As Tor offers levels of security, opt for Safe or Safest for peak anonymity, however, these settings may limit website compatibility. Configure a firewall to monitor incoming and outgoing traffic using Torr. Double-check the Https encryption of websites indicated by the lock symbol in the address bar. Ensure the websites you visit have URLs and be aware of unsolicited emails.
TOR VS Other Browsers
TOR Browser differs from other browsers such as Chrome, Firefox, Safari, and others principally because it prioritizes privacy and anonymity. However, several browsers declare anonymity and safety as their top concerns. We compare some secure browsers to Tor.
Tor vs i2p : The Invisible Internet Project and Tor are both decentralized and anonymous peer-to-peer networks.I2p is an anonymous overlay network that focuses on enabling the anonymous hosting of websites and services on its network.I2P is considered more safe than TOR but have more limitations.I2P only allows you to access specific websites, however Tor may also be used as a conventional browser.
Tor vs brave: Brave prioritizes privacy with features such as built-in ad blockers, tracker blocking, and HTTPS Everywhere. Brave is noted for its quick browsing speed and user-friendly interface. Tor prioritizes anonymity and privacy over speed. If you want more speed and little bit privacy, Brave is a good option.
Tor browser vs duckduckgo: DuckDuckGo prioritizes user privacy by not collecting search history or tailoring search results. Tor and Duckduckgo both aim to safeguard user privacy and security, but they utilize different methods. DuckDuckGo is for private search and better privacy on standard browsers, however it does not focus as much on anonymity as Tor.Tor browser vs VPN: Tor and VPN are both technologies for improving online privacy and security. VPNs encrypt the internet communication between your device and the VPN server.The basic objective of a VPN is to mask your IP address by routing your traffic through the VPN server’s IP address. VPN is appropriate for users who prioritize data security while maintaining higher internet speeds.
Is it safe to use Tor without VPN?
TOR sends your internet data across several nodes (relays), encrypting it at each stage. However, as already mentioned, TOR is not entirely secure. Using a well-known VPN can provide an added level of security. The VPN hides your IP address over that of the VPN server, further anonymizing your online activities. By combining a VPN and TOR, you can minimize the danger of traffic being intercepted at the exit node. Depending on the threat model and privacy considerations, you can configure TOR over VPN or VPN over TOR.
can tor browser be traced
Yes, TOR may be traced using many tools and expert understanding. State-level actors with significant resources can use traffic analysis and exploit gaps in the TOR network. Your privacy may be compromised on TOR if you log into identifiable accounts or use the same pseudonym across many services. Unpatched software, sometimes known as zero-day attacks, can be exploited to trace your identity. To use the TOR browser legally and anonymously, you must be aware of all the risks associated with it.
Final recommendation
The browser is a valuable tool for enhancing privacy and anonymity allowing users access to restricted content. It is generally safe to use however, the effectiveness depends on how it is used. To ensure safety best practices such as avoiding personal information revelation and keeping the browser updated should be performed.
